
How often do you go to a shop? With the ability to order items online and have them delivered within the same day, the retail experience has completely changed. We can get everything we need without moving from the couch. Pajamas on. Shopping mode engaged. Welcome to the digital age. But what does this mean for the retail industry?
75% of people shop online at least once a month. With consumers shopping from their phones, tablets, and computers, hacking and cyber invasions have become a serious threat in retail. As retailers fight to keep up with eCommerce demand, the size and cost of data breaches has grown.
As a retailer, it’s important to stay relevant. This means keeping up with current trends and meeting consumer needs. You can’t not be online. You will be overtaken by competitors and lose your customers. But you can’t allow your cybersecurity to lapse, either. Hacking can make you lose significant money. It can put your customers at risk. It can ruin your reputation. You must enhance your retail cybersecurity in this digital age.
What are the Cybersecurity Threats in Retail?
Before you learn about how to increase your business’s cybersecurity, it’s important to know the risks you might face. Whether you’re a small business selling on eBay or you have a large number of products and are competing with leading brands, cyber risks can occur at any level. Here are some of the most common threats to look out for:
Spam emails
Spam emailing isn’t the newest trick in the book; but it’s still effective. Spam emails are often the first step in the hacking process. Spammers rely on an employee opening a spam email, which might then allow them to gain access to bank details and other data. A spammer could be stealing your money - or that of your customers - under your nose. They might also install malware, causing your entire system to crash.
Spam emails are concerning, mostly because they aren’t always easy to detect. Your business computers will contain lots of confidential data, often collated and stored from your call center. Be aware of what spam emails look like and train all employees to click on anything with caution. Spam filters help, too.
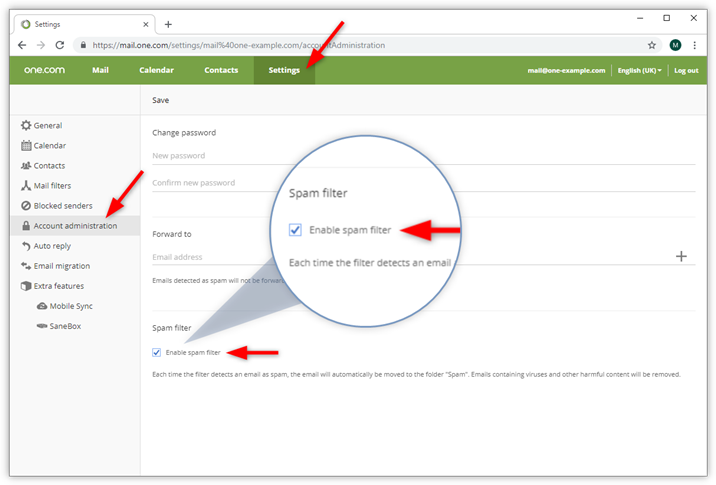 Source: help.one.com
Source: help.one.com
Refund Fraud
Refund fraud is another typical hacker trick. How does it work? There are a number of options, such as:
- A hacker creates a fake receipt, meaning that you give them the refund for a purchase they never made. Some fake receipts are sold on the dark web.
- Someone pays for an item using stolen credit card information, and then requests the refund to go onto a separate card.
- A person pretends their parcel never arrived, causing you to give them a refund. This often works if the person complains about your business on social media.
Refund fraud may not seem huge when it happens once or twice. But scammers and hackers can work at all levels and you could find yourself losing out on lots of profit.
Supply Chain Attacks
Most businesses work with supply chains. You might be sharing data and confidential information with a number of different vendors.
A supply chain attack is a cyber-attack that seeks to damage an organization by targeting less-secure elements in the supply network. Back in 2014, this happened to Home Depot, with more than 53 million email addresses stolen by cyber criminals through separate vendors.
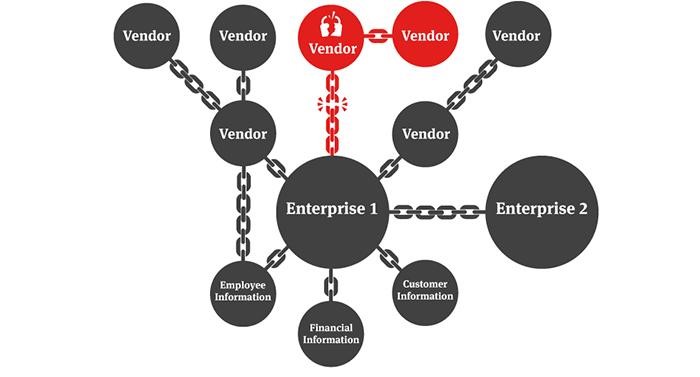
Source: nortonrosefulbright.com
Cybersecurity threats in retail are very real. But how do you stop them?
1. Regularly Update Software
First and foremost, it’s important to regularly update all software. Why? Older software might have vulnerabilities. Technology is increasingly advancing, and this means that developers are becoming more aware of cybersecurity. Once they’ve discovered a vulnerability in the software, they will push out an update online.
However, updates don’t always happen automatically. Many need to be updated manually. Your company might be sitting on several updates, meaning that your software is vulnerable and easy to be hacked. All software is connected, too. So, one piece of software with a vulnerability could impact your entire system.
Keep an eye on your entire operating system as well as the apps that you use. For instance, you can update your Mac both manually and automatically. Check to see if you have enabled the automatic update option on your Mac to avoid missing out on the latest security patches.
Take voice over IP software, for example. This relies on other VoIP protocols, like transmission control protocol for accuracy and user datagram protocol for speed. Any could become damaged. So, regularly updating software will benefit your business. The updates will be faster, more efficient, and iron out any errors. SD-WAN can help with this, too.
2. Use the Cloud
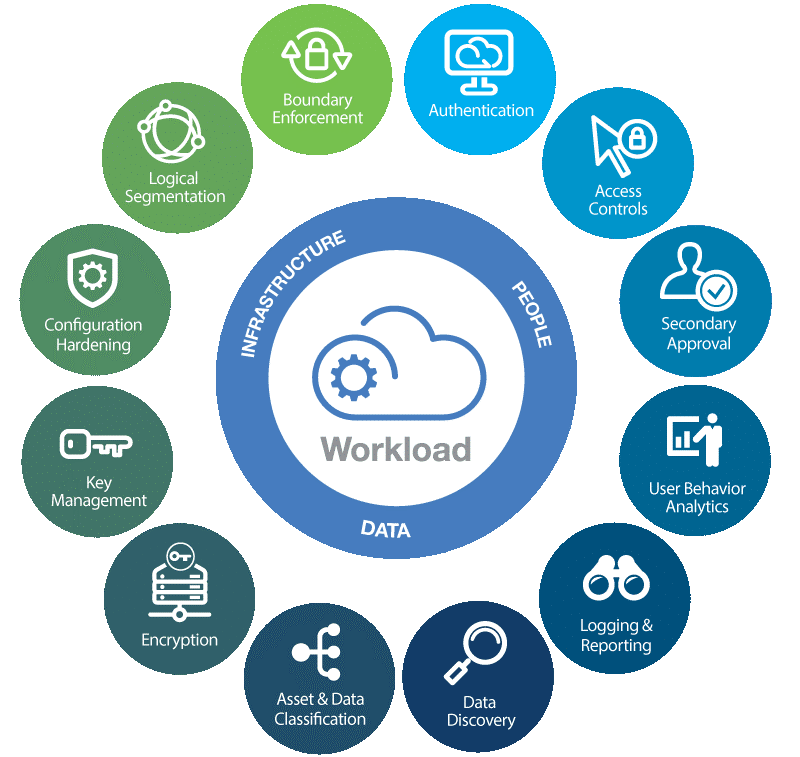 Source: Kinsta.com
Source: Kinsta.com
Some retailers worry about getting onto the cloud. With all data in one place, cloud security breaches can have serious repercussions.
However, there are many security benefits when using a cloud-based system. Most have integrated security systems to protect sensitive information and transactions, preventing a third party from eavesdropping or tampering with data being transmitted. The security benefits of cloud-based systems include:
- Firewalls. These protect the perimeter of your network security and your end-users. They also safeguard traffic between different apps stored in the cloud.
- Threat intelligence. This is smart technology that spots security threats and ranks them in order of importance.
- Data masking. This encrypts identifiable information, such as names. It helps to maintain integrity by keeping certain information private, making breaches less likely to occur.
- Access controls. These protect data by allowing you to set access lists for different assets. Many retailers only allow specific employees to access certain files. This means that only certain people will be able to access certain information, and you can keep a better track of any breaches to prevent confidential data from being leaked.
- Disaster recovery. In the case of lost or stolen information, this is key. It helps to recover the information.
Using a cloud-based system will also ensure you have the best software - which might be updated automatically. A Cloud Workload Protection Platform (CWWP) plays a crucial role in protecting workloads in hybrid cloud environments. It offers tailored security measures designed specifically for cloud-native applications, ensuring robust protection across multiple cloud infrastructures. Keeping all confidential data in one place is essential to tight-knit cybersecurity that keeps scammers and hackers at bay.
3. Keep your Mobile App Secure
Back in 2017, Rich Jones, head of product and UX at Asos, said, “we need to build experiences that capitalize on mobile. We’re designing experiences that are essentially right for the customers’ devices because their entire lives are here. How do we make sure our experience matches that?” Getting 58% of customers to buy on the app, Asos is an example of a mobile app success story.
Source: Pinterest.co.uk
But Asos isn’t the only retailer that uses mobile apps to manage and increase purchases. The mobile app is one of the biggest changes in our digital age. Customers can access products more easily and it unifies online and in-store shopping experiences. Easier browsing means easier buying.
Mobile apps also help with your marketing strategies, as you can access data that allows you to customize shopping experiences. Automated customer service can also be integrated, making for a more streamlined system.
However, the great addition of the mobile app brings an increased risk of data breaches. An app lives on a person’s phone, meaning that it is always active. It’s a vulnerability. So, it can be difficult to ensure this protects consumer information. How can you solve this? Your apps will need the following:
- Secure code. Developers must ensure that there are no weaknesses in their code that hackers could access. Again, this is why you must regularly update your software, in case vulnerabilities are detected.
- Payment integrations must follow correct practices. PCI released these guidelines for a reason: to keep people safe.
- Regulations on what data to collect. While data can be useful, the more you collect, the easier it is to breach - and the more tempting it becomes to the wrong people. Only collect information that is useful to you and will benefit your business.
Don’t let your mobile app be your downfall. When done well, it can be a great asset to your business. When done badly, it can be a security disaster.
4. Focus on Third-Party Security
We’ve already heard about Home Depot’s third-party disaster. But it’s not the only company that experienced such problems. Amazon, T-Mobile, eBay, Macy’s, and Target are among other companies who have experienced third party data breaches, showing just how common they can be.
There’s simply no point focusing on your own security if it gets breached through your third-party vendors. It’s money and time wasted. But what can you do?
Retailers need to operate a continuing monitoring solution where they keep an eye on third party vendors. Security ratings will ensure you are kept up to date with your vendors’ security performance. If their performance is bad? It might be time to find another.
You probably have a good relationship with your third party vendors, regularly communicating and checking in (try using a VoIP conferencing phone to improve the quality of your conference calls). But this doesn’t mean you shouldn’t check up on their security system. If their security is weak, it will affect you. So make sure you monitor closely.
5. Train your Employees
You can also enhance retail cybersecurity by making sure your employees are following protocols. Data breaches can happen by accident, when an employee isn’t paying close attention, or makes a simple mistake. The internet means that one small action can have huge consequences — like clicking on spam.
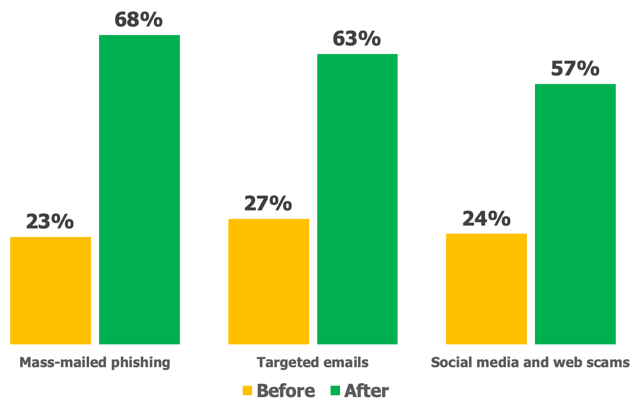 Graph from infosecinstitute.com shows the percentage of IT/security professionals reporting employees as “capable” or “very capable” of recognizing cyber attacks before and after training.
Graph from infosecinstitute.com shows the percentage of IT/security professionals reporting employees as “capable” or “very capable” of recognizing cyber attacks before and after training.
It’s important to ensure that all employees follow proper practices and know how to behave when something is awry. As an employer, it is your responsibility to make them invested in the process and want to keep the company safe. This means ensuring they have the proper training in all equipment and keep any passwords safe.
It also means ensuring that you are managing them correctly. Skill-based routing can be a great way to establish their skills and match the right agents to the right customers in a call center setting. You should also ensure that employees are collaborating effectively and understand teamwork. The best video conferencing software can help. Employees who feel respected want to create a cyber secure retail environment and protect their customers.
6. Have a Data Breach Recovery Plan
All good retailers have a data breach recovery plan. This does what it says on the tin. It’s your guide to the next steps if a data breach occurs. Not sure how to make one? Good ones look something like this:
- Stop the breach: you can’t recover anything until the breach has been stopped. This will most likely involve isolating all systems and separating the breached user accounts. Eliminating the threat is your first priority.
- Assess the damage: Once the breach has been stopped, you’ll need to assess the damage and determine how this will affect your business.
- Notify the persons involved: it’s not pleasant, but you will need to notify anyone who was involved in the breach or who could be impacted as a result. This will most likely mean an email campaign.
- Security check: now that those involved have been notified, you will need to run a security audit. This will involve analyzing all software and will hopefully determine where the breach came from.
- Update for the future: Once you’ve had one data attack, another could follow. So, you’ll need to update your plan for the future. Do employees need more training? Do you need to update software more often? Learn from your mistakes and grow stronger.
7. Question your customers
The customer is always right. It’s something employers have been saying for years. But is it really the case?
We all want to show customer appreciation. But the fact is that while most of your customers want to buy your products, some have ulterior motives. The customers forging receipts; the customers faking orders that didn’t arrive; the customers sending spam. Customers can be hackers in disguise.
So, while it’s good to be trusting, working in retail means taking things with a pinch of salt. It means learning to question and check. So, while you’re training your employees, teach them to be cautious. If a customer is asking to see a screen or seems like they’re distracting you - it might well be for an unfortunate reason. Before you or employees start giving out data, stop and think.
Employees who know how to question customers mean that you spend less time worrying about them and can focus on other areas of your business, such as managing your sales pipeline. Top project management tools can help with this further.
 Image from Unsplash.com
Image from Unsplash.com
Enhance your Retail Cybersecurity — Now
Retail cybersecurity can feel overwhelming at first. The internet is constantly evolving and people are finding new ways to access information and damage businesses.
However, there are ways to enhance your cybersecurity. They are worth investing in. For the sake of your business, make sure you do.





Leave a reply or comment below